Why You Need Unified Entitlements
Understand the risks with access rights to your organization and how addressing Unified Entitlements will yield meaningful and immediate value for your organization.
What We Offer
Explore our end-to-end capabilities and services around Unified Entitlements, from initial strategy through enterprise oversight and implementation.
Learn More
Go into depth on our Unified Entitlements methodologies and explore our thought leadership on this and related topics.
Successful enterprise solutions, ranging from Generative AI, to Semantic Layers, to Enterprise Search are intended to allow the RIGHT people to see the RIGHT information at the RIGHT time. As these solutions come to fruition, the importance of adequately securing information assets is compounded. This securing of information assets is called entitlements and it is quickly becoming one of the biggest issues and risks for organizations.
Our answer to this risk is Unified Entitlements.
Unified Entitlements provide a holistic definition of access rights, enabling consistent and correct privileges across every system and asset type in the organization.

Why You Need Unified Entitlements
Organizations big and small are pouring their resources into uniting their disparate sources of content, data, and information (what we collectively call knowledge assets). Generative AI and Semantic Layers have helped to make this long standing goal a reality for many organizations, but with it, an old challenge is resurfacing in troubling new ways. Many organizations have avoided a high-risk burning topic – access and identity management of the various content, data, and information assets that are now being more automatically surfaced. Failure to address this risks massive exposure for the organization.
Imagine an employee finding an outdated version of a safety directive and accidentally acting on it, causing harm to the company and even worse, to the individual. Or consider what would happen when a new Generative AI solution “repackages” old and incorrect content to make it look new, including it in an answer that your employees or customers are using to make a decision. Furthermore, consider the implications of currently unsecured, but hidden, classified or sensitive information being exposed by your organization’s new semantic and AI capabilities. All of these are likely realities without a strategy for Unified Entitlement.
What We Offer
From initial strategy through to enterprise-level development and implementation, we offer a range of Unified Entitlement services to address your organization’s priorities:
- UE Audit – Our consultants can review your systems and information practices to identify the scope of your entitlements issues. We will provide your team with a report that can be used to put the focus on this important issue.
- UE Strategy – Entitlements issues can be overwhelming. Our consultants can help your organization understand the scope of the problem and provide a roadmap with targeted recommendations for bringing your organization into compliance.
- Tool Evaluation and Selection – The right tool can make or break an implementation initiative, and this is no different for a unified access solution. We monitor the current and planned capabilities of tooling options on the market so that we can advise our clients on the best solutions for their specific needs.
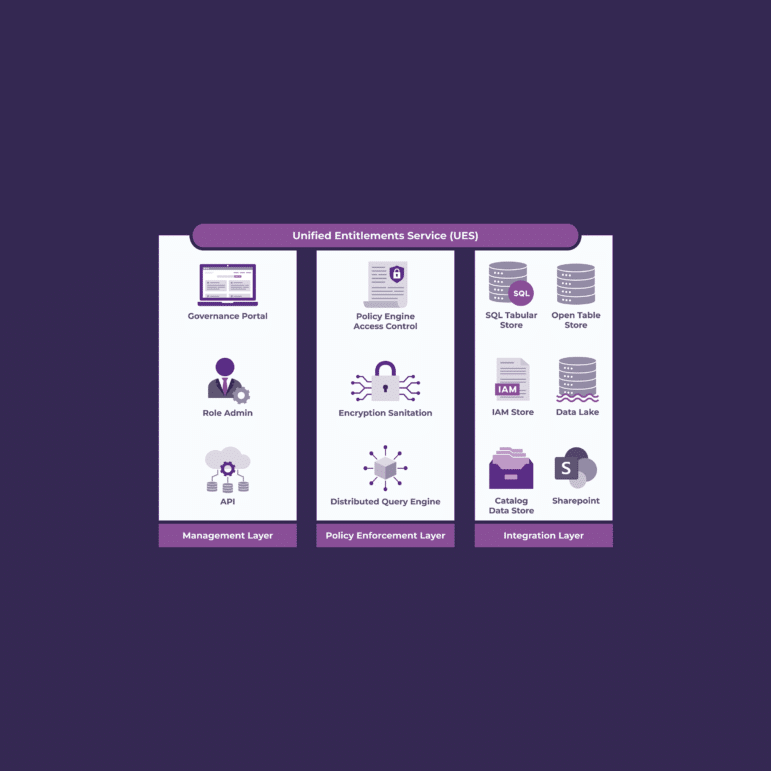
- Unified Access Modeling – Entitlements rules need to be modeled so that they can be implemented across the users and systems that need to respect entitlements. The rules governing how entitlements are implemented are often a combination of attribute- and role-based access. Each repository may have its own method for implementing entitlements. All of this creates complexity in how a single security model can be implemented.
- UE Architecture – An entitlements solution must be designed to fit within the existing enterprise infrastructure of an organization. The final solution needs to integrate with your identity and access management systems, as well as all of the data and content repositories for which the access permissions need to be applied.
- Development and Implementation – A key piece of entitlements management is ensuring that the tailored solution is properly implemented in your environment so that adjustments and future updates can be handled automatically.
"*" indicates required fields
