Today’s enterprises face a perfect storm in data access governance. The shift to cloud-native architectures has created a sprawling landscape of data sources, each with its own security model. For example, a typical enterprise might store customer data in Snowflake, operational metrics in PostgreSQL, transactional records in MongoDB, and unstructured content in Microsoft Teams—all while running analytics in Databricks and feeding AI systems through various pipelines.
Effective management of information access across the enterprise is one of the most difficult problems that large organizations deal with today. Unified entitlements offer a solution by providing a comprehensive definition of access rights, ensuring consistent and correct privileges across every system and asset type in the organization.
A Unified Entitlements Service (UES) addresses these challenges by creating a centralized policy management system. It translates high-level business rules into controls specific to each platform. UES acts as the universal translator for security policies, allowing governance teams to define rules once and apply them everywhere.
A strong UES consists of several interlocking components that work together to provide seamless policy enforcement while still respecting each platform’s native security model. The diagram below illustrates how these components interact in a comprehensive UES implementation:
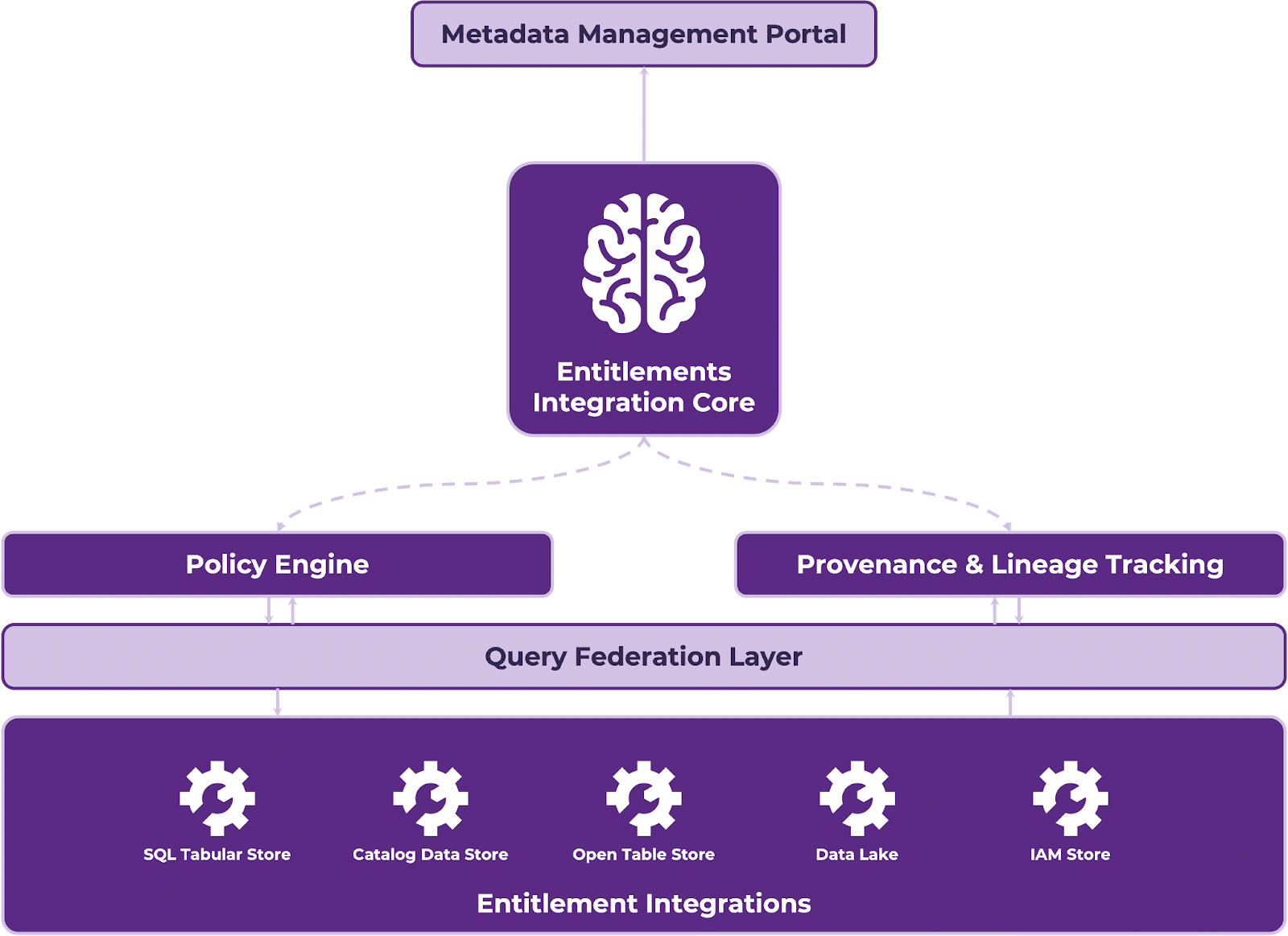
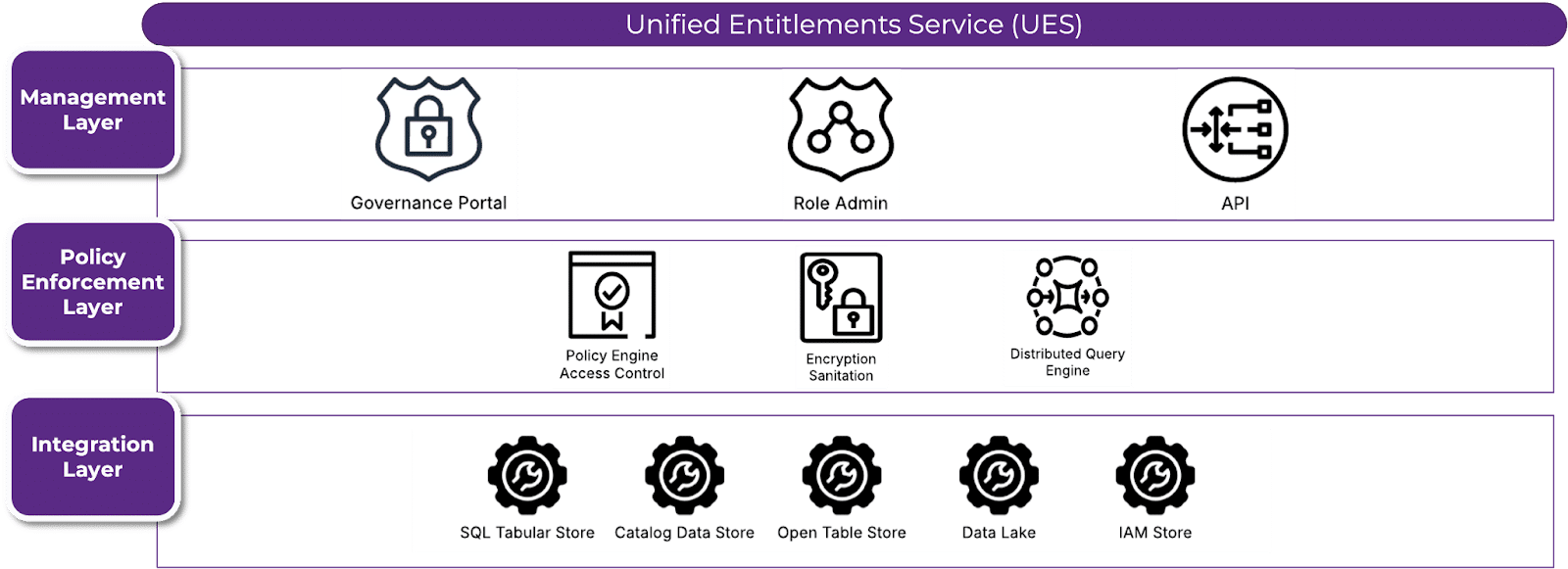
Figure 1. High-level architecture of a Unified Entitlements Service showing the key components and their interactions
The Core Components
Entitlement Integration Core: This stateless microservice cluster serves as the brain of the UES, managing the complex relationships between users, roles, and permissions. It utilizes high-performance caching (typically implemented with Redis or similar technologies), it provides entitlement lookups to maintain performance.
Policy Engine: Built on frameworks like Open Policy Agent (OPA), this component evaluates access requests against enterprise-wide policies expressed in a domain-specific language. For example, a policy might state: “Users in the Marketing department can access customer demographic data, but not payment information, unless they also belong to the Finance team and are working on the Q4 campaign.”
Provenance & Lineage Tracking: Every access decision is logged with comprehensive context, creating an immutable audit trail for compliance and security investigations. Implementations typically leverage systems like Apache Atlas alongside Kafka Streams for real-time audit logging.
Query Federation Layer: Beyond simply enforcing access at the resource level, advanced UES implementations apply entitlements directly to query execution. Using technologies like Trino (formerly PrestoSQL) with custom connectors, the system can modify queries in-flight to add entitlement-aware filters.
Entitlement Integrations: These connectors translate UES decisions into platform-specific access controls within native Identity and Access Management (IAM) systems. This typically involves the use of OAuth 2.0 and SAML for authentication flows.
Metadata Management Portal: A user-friendly interface empowers governance teams to define, test, and monitor entitlement policies. Modern implementations often use React-based front-ends with GraphQL APIs to provide a responsive management experience.
The Lifeblood of UES: Entity Resolution
At the heart of effective entitlement management lies a critical challenge: accurately resolving user identities across disparate systems. A single individual might exist as three distinct identities, such as:
- john.smith@company.com in Azure AD
- jsmith_finance in Snowflake
- employee_456789 in AWS IAM
Without proper resolution, John might inadvertently gain excessive privileges through the combination of his separate identities or face frustrating access denials where legitimate access should be granted.
A sophisticated UES employs entity resolution algorithms—combining deterministic matching rules, probabilistic methods, and sometimes machine learning—to create a unified identity graph. Products like Senzing are designed for this very purpose. This graph connects all representations of a user across systems, enabling consistent policy enforcement regardless of which system they’re accessing.
The resulting unified user profile might look like this:
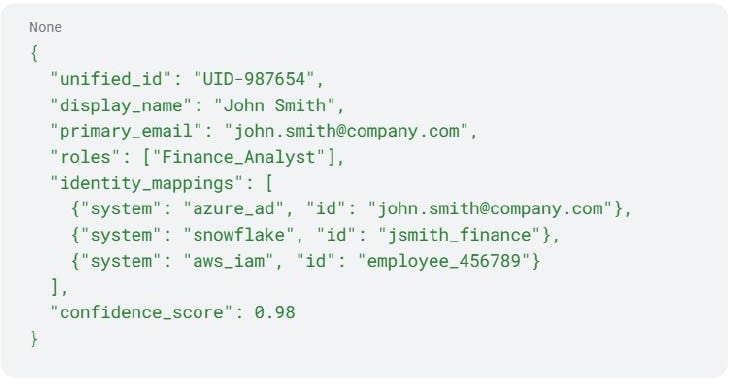
This unified view becomes the foundation for consistent entitlement decisions across the entire data ecosystem.
Architectural Pattern for Enterprise Deployment
Federated Enforcement with Local Agents
The Unified Entitlement Service employs a layered and federated architecture designed for scalability, interoperability, and governance across enterprise data environments. At its core, the system is structured into distinct layers, each responsible for key functions:
- Entitlement Integration Core Service (EIS) manages access control, policy enforcement, and lineage tracking.
- Metadata Management Service ensures governance and transparency.
- Query Federation enables distributed query execution.
- Entitlement Integrations provide seamless access to diverse data sources.
This architecture diverges from the traditional hub-and-spoke model, operating as a federated governance framework. In this model, entitlement decisions are enforced dynamically across multiple platforms without centralizing sensitive data. The Distributed Query Engine plays a crucial role in aggregating results across entitlement sources, ensuring that governance policies are applied at the time of query execution.
Real-World Implementation Challenges
Despite its compelling benefits, implementing a UES presents significant challenges that organizations must carefully navigate.
Case Study
In recent work with a large global investment firm, we implemented role-based access control (RBAC) and attribute-based access control (ABAC) as one component of a unified entitlements solution. In this work, graph data was persisted in a Neo4j database. Read and traversal entitlements for properties were implemented to control what nodes were discoverable, and what properties of nodes were viewable in downstream applications. Through single sign-on (SSO) connections to Neo4j, a UES can maintain awareness of data source grants while implementing higher level entitlements.
Policy Drift
Without proper controls, UES policies may diverge from actual platform rules. For example, a database administrator might make an emergency change directly in PostgreSQL, bypassing the UES. Over time, these discrepancies accumulate, creating security gaps.
Solution: Implement continuous compliance scanning that compares actual platform entitlements against UES policies, flagging and remediating discrepancies.
Performance Considerations
Real-time entitlement validation adds overhead to data access requests. For analytical workloads processing billions of records, even milliseconds of added latency per decision can significantly impact performance.
Solution: Employ a hybrid approach that combines pre-computed access decisions for common patterns with just-in-time validation for edge cases. Aggressive caching of entitlement decisions can reduce overhead to negligible levels for most scenarios.
Organizational Alignment
Perhaps the most overlooked challenge is organizational: UES crosses traditional boundaries between security, data, and platform teams. Without clear ownership and governance, implementation efforts can stall amid competing priorities.
Solution: Establish a federated governance model with representatives from security, data management, compliance, and platform engineering. This cross-functional team should own the UES strategy and roadmap, ensuring alignment across organizational boundaries.
The Future of Unified Entitlements
As UES technology matures, several emerging trends point to its future evolution:
AI-Driven Entitlement Intelligence: Advanced UES implementations are beginning to incorporate machine learning to detect anomalous access patterns, suggest policy improvements, and automatically remediate compliance gaps. These capabilities will transform UES from a passive enforcement layer to an active participant in security governance.
Context-Aware Access Policies: Next-generation entitlement systems will incorporate contextual factors beyond identity—such as device health, location, time of day, and behavioral patterns—to make more nuanced access decisions. For example, a finance analyst might have full access to sensitive data when working from corporate headquarters but receive masked results when connecting from a coffee shop.
Federated Multi-Cloud Governance: As enterprises adopt multi-cloud strategies, UES will evolve to provide consistent governance across cloud boundaries, ensuring that security policies remain portable even as workloads move between environments.
Conclusion: A Services Based Approach
Managing entitlements in a consistent manner across all of your applications, both on-premises and in the cloud, feels like an impossible challenge. As a result, many organizations avoid the problem, hoping it will resolve itself. A services-oriented approach like the one that described above makes solving this problem possible. If you would like to learn more about how this works and how you can solve entitlements at your organization, please email us at info@enterprise-knowledge.com.
