The importance of data governance grows as the number of users with permission to access, create, or edit content and data within organizational ecosystems faces cumulative upkeep. An organization may have a plan for data governance and may have software to help them do it, but as users cycle by 10s to 1000s per month, it becomes unwieldy for an administrator to manage permissions, define the needs around permission types, and ultimately decide requirements that exist for users as they come and go to access information. If the group of users is small (<20), it may be easy for an administrator to determine what permissions each user should have. But what if thousands of users within an organization need access to the data in some capacity? And what if there are different levels of visibility to the data depending on the user’s role within the organization? These questions can be harder for an administrator to answer themselves, and cause bottlenecks in data access for users.
An entitlement management model is an important part of data governance. Unified entitlements provide a holistic definition of access rights. You can read more about the value of unified entitlements here. This model can be designed and implemented within a semantic layer, providing an organization with roles and associated permissions for different types of data users. Below is an example of an organizational entitlements model with roles, and explanations of an example role for fictional user Carol Jones.
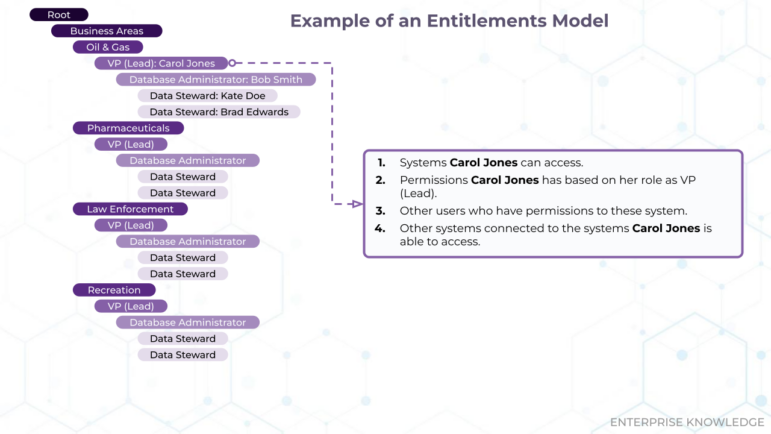
Having a consistent and predictable approach to entitlements within a semantic layer framework makes decisions easier for human administrators within a data governance framework. It helps to alleviate questions around how to gain access to information needed for projects if it is not already available to a user, given their entitlements. Clearly defined, consistent, and transparent entitlements provide greater ease of access for users and stronger security measures for user access. The combination of reduction in risk and reduction in lost time makes entitlements an essential area of any enterprise semantic layer framework.
An entitlement management model addresses the issue of “which users can do what” with the organization’s data. This is commonly addressed by considering which users should be able to access (read), edit (write, update), or create and delete data, often abbreviated as CRUD. Another facet of the data that must be considered is the visibility users should have. If there are parts of the data that should not be seen by all users, this must be accounted for in the model. There may be different groups of users with read permissions, but not for all the same data. These permissions will be assigned via roles, granted by users with an administrative role.
C=Create, R=Read, U=Update, D=Delete
One method to solve this problem is to develop a set of heuristics for users that the administrator can reference and revise. By having examples of the use cases that they have granted permissions for, they can reference these when deciding what permissions to grant new users within a model, or users whose data needs have evolved. It is difficult to predict all individual user needs, especially as an organization grows and as technology advances. Implementing a set of user heuristics allows administrators to be consistent in granting user permissions to semantically linked data. They are able to mitigate risk and provide appropriate access to the users within the organization. The table below shows some common heuristics, who to apply them to and a decision if the entitlements needs further review. A similar approach is the Adaptable Rule Framework (ARF).
This method serves as a precursor to documenting a formal process for entitling, which should include the steps, sequence, requirements, and timeliness in which users are entitled to access data augmented by a semantic layer. These entitlements will determine where in the semantic layer framework users can go and their ability to impact the framework through their actions. Decisions and documentation of these process elements provide thorough consistency within an organization for managing entitlements.
Enterprise Knowledge (EK) has over 20 years of experience providing strategic knowledge management services. If your organization is looking for more advice for cutting-edge solutions to data governance issues, contact us!






